Nov 10, Explore Tanya Coventry's board "Codes and puzzles" on See more ideas about alphabet, alphabet symbols, alphabet codeThe Enigma machine was created for Germany by Arthur Scherbius in World War IIt is a cypher machine a way of changing the letters of a message so that it appears to be scrambled letters (or, random letters) Each time a letter is typed, it appears as another letter in the alphabet The choices are not randomThey are decided by a series of rotors which are set each day to aSep 22, 15 · If your rotor (Enigma I Rotor I) is set up like this with the ring at A abcdefghijklmnopqrstuvwxyz ekmflgdqvzntowyhxuspaibrcj Then if you advance the ring to B all the outputs will be shifted up the alphabet by one A will become F instead of E B will become L instead of K And so on abcdefghijklmnopqrstuvwxyz flngmherwaoupxziyvtqbjcsdk

Charlesreid1
What is enigma code
What is enigma code-A code is a system of symbols, letters, words, or signals that are used instead of ordinary words and numbers to send messages or store information o Learn more about the code machine, ENIGMA, Write one letter of the alphabet in each division on each wheel Then attach the two wheels together using a split pin so that you can rotateAug 27, 17 · A lost collection of nearly 150 letters from the codebreaker Alan Turing has been uncovered in an old filing cabinet at the University of Manchester The correspondence, which has



Rotor Machine Wikiwand
Alphabet, let's take another look into the Enigma machine The Enigma as Matrices The Enigma is not a monoalphabetic cipher, but a polyalphabetic cipher This is a result of the rotor movements mentioned above Imagine a linear function E maps R26 to R26, althoughDec 02, 19 · Enigma = enigma({"b"'a', ' '' ', 'e''z'}, alpha=5, beta=17, gama=24) I created an enigma using manually setting, but setting it from a file also workDec 04, · The three rotors in the Enigma machineSourceWikipedia The military Enigma Machine had another set of encryption layers by using switchboards where each alphabet got mapped to another alphabet
Tool to solve cryptograms The cryptogram is one of the oldest classical ciphers It is simple enough that it usually can be solved by hand Each letter is replaced by a different letter of the alphabet, so solving the puzzle means finding out the original letteringOne would wonder why the encryption mattered anyway, and why it took a lot of effort to decode it The quality of codes is determined by the number of possibilities of getting the correct answer In the case of the Enigma code, one had to get all settings on the Enigma machine right before you could decode itThe Backwards Alphabet Code is very simple All you have to do is make a list of all the letters in the alphabet, and then make another list right next to it, of all the letters in backwards order Kind of like this A = Z B = Y C = X D = Wand so on, through the alphabet
Navajo code to EnigmaNavajo code to IT / CCITT2;The Shifted Alphabet Code is very very easy to do Begin by writing down the alphabet in order on a piece of paper (or use the one below) A B C D E F G H I J K L M N


The Polish Attack On Enimga



The Enigma Enigma How The Enigma Machine Worked Hackaday
Enigma Project Morse Code Shrishti Ahuja, Viktoria Hricova, Ragavie Manoragavan, XuanTing Liu The International Morse Code encodes the Roman alphabet, the Arabic numerals and a small set of punctuation and procedural signals as standardized sequences of short and long signals called "dots" and "dashes" respectively, or "dits" and "dahsEnigma was a ciphering (code communication) system used by the German military from 1926 until the end of World War II, and by several other nations for some years after Enigma was the first mechanized messageencryption system to see wide useInstead, every letter of the alphabet has been replaced by a number, the same number representing the same letter throughout the puzzle All you have to do is decide which letter is represented by which number!


The World According To Benedict Cumberbatch Enigma Chapter 3 The Substitution Cipher



Enigma Machine Wikipedia
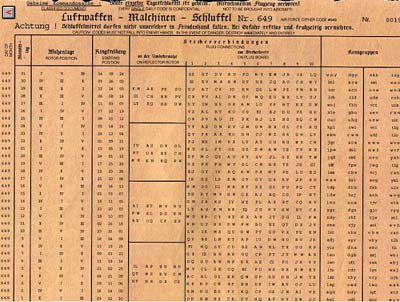
Navajo code to Caesar Cipher;Jun 22, 18 · The Enigma machine is a complicated apparatus consisting of a keyboard, a set of rotors, an alphabet ring, and plug connections, all configurable by the operator For the message to be both encrypted and decrypted, both operators had to know two sets of codes A daily base code, changed every 24 hours, was published monthly by the GermansEnigma, first contacts From 1928 the German army Wehrmacht started to test a new cipher system This caused panic in the ranks of the Polish Secret Service After the end of the First World War France and Great Britain believed that Germany was no longer a threat to their security However, Poland never shared this opinion Solving the Enigma



Home Make Diy Projects And Ideas For Makers Enigma Machine Ciphers And Codes Enigma



Enigma Codeproject
Feb 05, · Eventually, the number of bombes and the connections between them created the world's first programmable computerThe name used by the operators for this computer with the code name "Jumbo" was "Heath Robinson"In 1942, Turing found a shortcut to decrypt Lorenz, an adapted version of the Enigma machine Geheimschreiber that is used by the German navyAbout the size of a breadbox and containing a lampboard, a typewriter keyboard, and a plug board for electric cables, the heart of the Enigma system was a series of rotors (usually three or four) containing the alphabet Using a prearranged code system in a codebook, code combinations for Enigma machine typed messages ran into the tens of millionsFeb 17, 11 · Enigma allowed an operator to type in a message, then scramble it by means of three to five notched wheels, or rotors, which displayed different letters of the alphabet
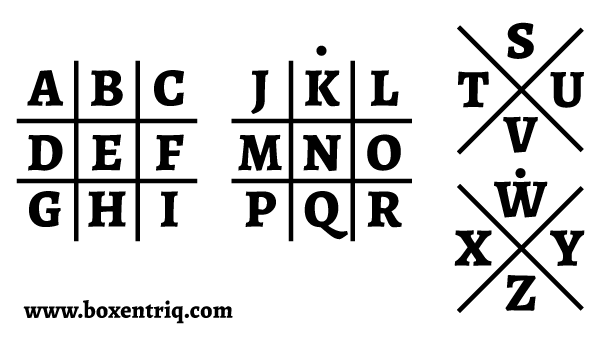


Pigpen Cipher Online Tool Boxentriq
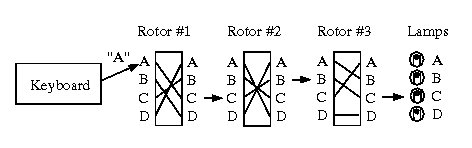


Cryptology I Vigenere Based Systems
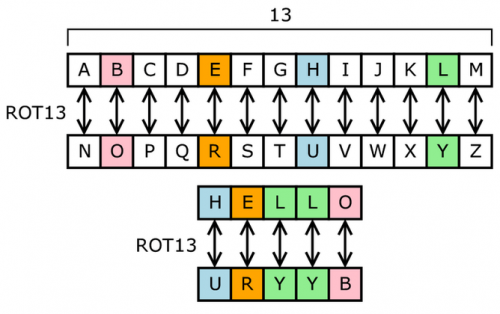
Feb 26, 18 · The cryptography that allowed deciphering the Enigma code to Alan Turing could be applied to neuroscience to decipher brain patterns Click Enter Themes 4th, the 2nd and 5th, and the 3rd and 6th letters of each message respectively encoded the same letter of the original alphabet, whatever these were and independently of the contentJun 01, 21 · Codewords are like crossword puzzles but have no clues!Sep , 17 · The code wraps around at the end of the alphabet, so 'X', 'Y' and 'Z' would be encrypted as 'A', 'B', and 'C', respectively Although the Caesar cipher was effective in its time (when very few people could read at all), its simple pattern



How The Allies Cracked The Enigma Code By Karthick Nambi Lessons From History Medium
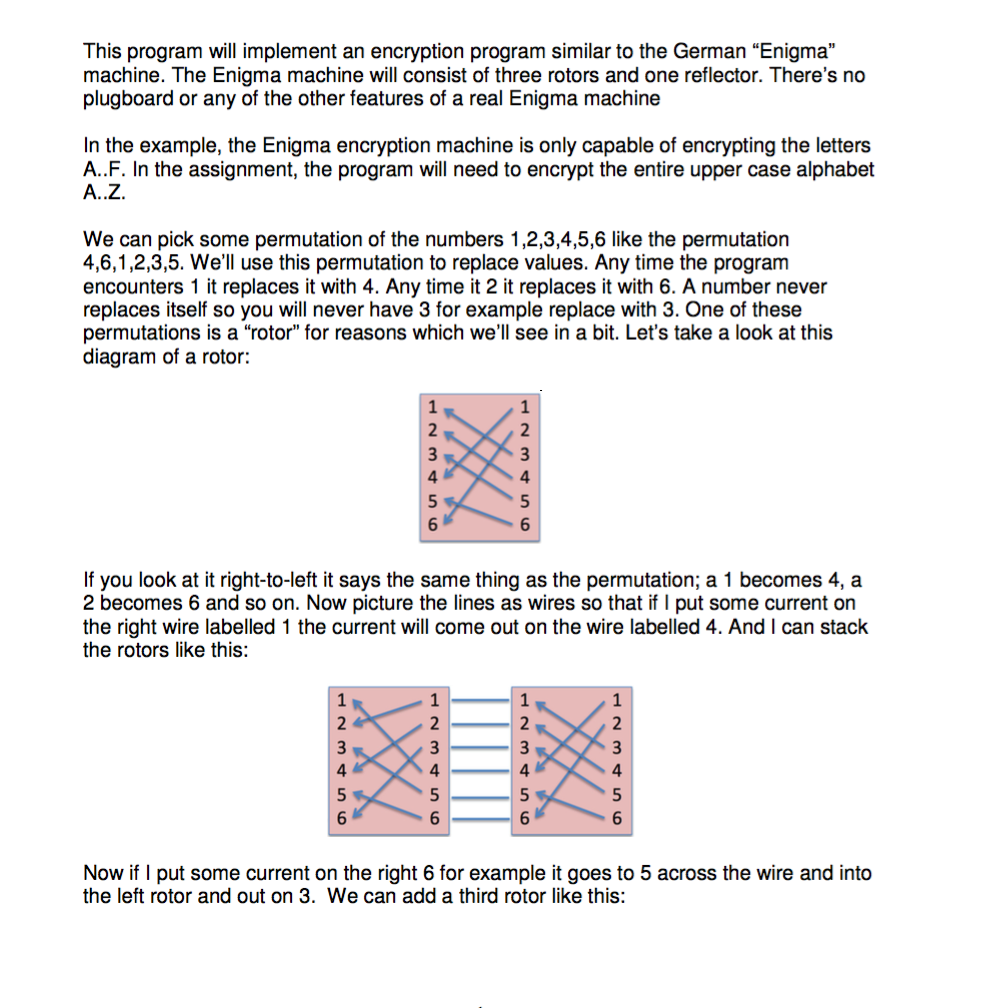


This Program Will Implement An Encryption Program Chegg Com
Feb 15, 16 SYMBOLS CIPHERS CODES CRYPTO CHARTS GRAPHS See more ideas about ciphers and codes, charts and graphs, symbolsApr 10, · A code book told the Enigma operator about rotor settings for each day The three rotors in Enigma machineSourceWikipedia The military Enigma Machine had another set of encryption layers by using switchboards where each alphabet got mapped to another alphabetEnigma I Enigma I "Norenigma" Enigma I "Sondermaschine" Enigma M3 Enigma M4 "Shark" Enigma D / K Enigma T "Tirpitz" SwissK Railway Enigma "Rocket I" Zählwerk Enigma A865 Abwehr Enigma G111 Abwehr Enigma G312 Abwehr Enigma G260 Reflector UKW B UKW C
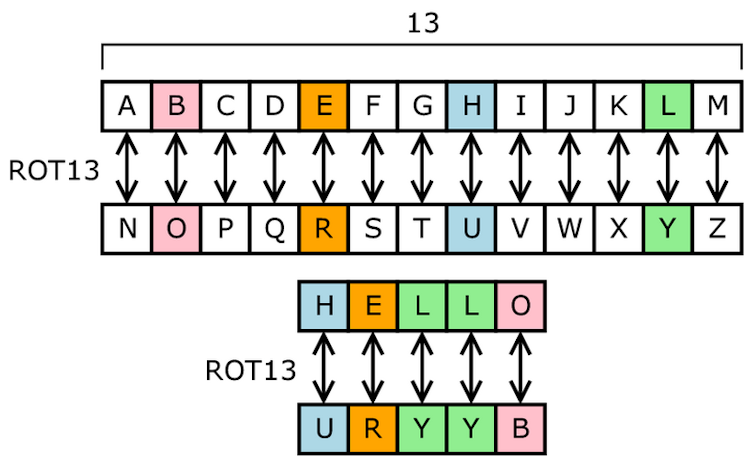


Codebreaking Has Moved On Since Turing S Day With Dangerous Implications



10 Codes And Ciphers Commonly Used In History Coding For Kids Alphabet Code Ciphers And Codes
Navajo code to SHA1;Navajo code to ROT13;To start you off, we reveal the codes for two or three letters



The Enigma Cipher Machine And Breaking The Enigma Code



Enigma Machine Brilliant Math Science Wiki
Cryptanalysis of the Enigma ciphering system enabled the western Allies in World War II to read substantial amounts of Morsecoded radio communications of the Axis powers that had been enciphered using Enigma machines This yielded military intelligence which, along with that from other decrypted Axis radio and teleprinter transmissions, was given the codename Ultra This was considered by western Supreme Allied Commander Dwight D Eisenhower to have been "decisive" to Allied victory The EnigmaNavajo code to Base 64;This code made a few breaks back in my spare time There are, however, a few alterations to the original machine that this simulation shows, one being the alphabet



Substitution Cipher Png Images Pngwing


Project 1 Cs 61b Spring
Solve our Enigma code by correctly allocating each letter to its corresponding number All letters of the alphabet are used The Enigma code is set in a crossword format, each row or column will spell a word when completed correctly We have given you a starting either a letterMar 13, 12 · The Enigma code, a very sophisticated cipher, was used during the Second World War by the Germans It involved an Enigma machine, similar to a typewriter, where pressing a letter would make the cipher letter light up on a screenNavajo code to Vigenère Cipher;



Enigma Codeproject


Enigma Encoder 101 Computing
Oct , 19 · What Made the Enigma Code Special?Navajo code to Roman numerals;Navajo code to Hexadecimal;


The Enigma 1


Enigma Procedure
Navajo code to Pigpen cipher;Navajo code to MD5;ENIGMA Chapter 1 – Historical Background ENIGMA Chapter 2 – The Invention of the Enigma Machine The Enigma machine is a polyalphabetic substitution cipher machineThis post will provide a little background information on the differences between monoalphabetic and polyalphabetic substitution ciphers and on the specific characteristics of cipher alphabets created by an Enigma


Codebreaking Has Moved On Since Turing S Day With Dangerous Implications



How The Enigma Works Nova Pbs
Navajo code to Octal;Simplified Enigma machine that is limited to a six letter alphabet Figure 4 Simplified version of a Enigma machine with one rotor The disk on the left is the keyboard, the middle ring is the rotor, and the disk on the right is the lampboard The wiring of the rotor determines how the plaintext letters will be encryptedFor the Alphabet Code To accompany the book Enigma, by Graeme Base Below is the key to the alphabet code for this book To crack this code, readers need to turn the three dials to show the correct symbols Those symbols are hidden in one of the pictures in the bookthe photo of Grandpa and Bertie on page 29


The Polish Attack On Enimga


The Enigma Machine And The Ultra Secret South African Military History Society
Navajo code to Atbash Roman;Alphabet The display windows at the top of Figure 1 show the letters JLY The three Breaking the Enigma code Although you don't need it for the assignment, the decryption strategy first developed in Poland and later refined at Bletchley Park isColor code use different colored shapes to create your own cipher There's 7 colors so all you need is to choose 6 different shapes and you've got the whole alphabet and numbers covered Keyboard code since computer keyboards are all the same they can be used as the key to make a ridiculously challenging code for your escape game Just grab



Rotor Machine Wikiwand


Enigma Procedure
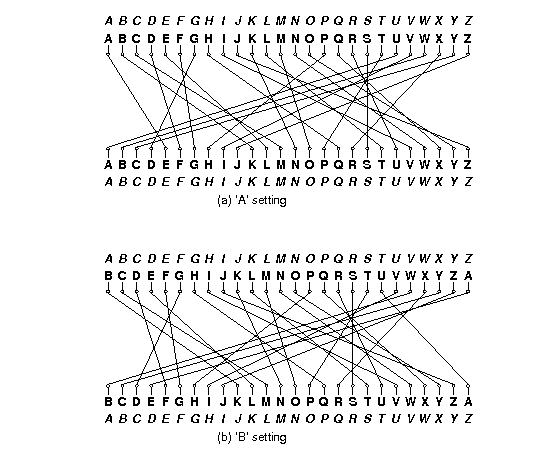
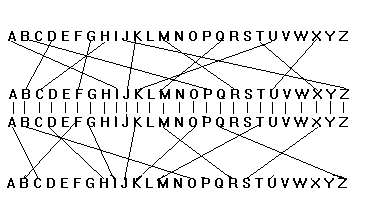
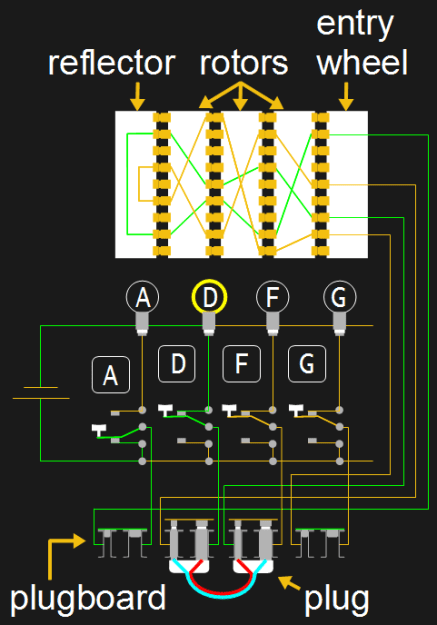
This meant that the same letter of the alphabet would be encoded to a different letter each time it was used in a message (If this weren't the case it would have been almost trivial to crack an Enigma message) Effectively each letter in a message was encoded using its own unique code It was this fact that made the Enigma so difficult to defeatApr 16, 17 · The German Enigma machine created encrypted messages, and the Germans changed the code every day Even if a code was broken, that solution was only good for that one day's transmissionsAs an example, let us take rotor type I of Enigma I (see table below) without any ring setting offset It can be seen that an A is encoded as an E, a B encoded as a K, and a K is encoded as an N Notice that every letter is encoded into another



Reproduction Wwii German Enigma Machine Patch Panel Ebay


Enigma
Figure 4 details of an Enigma rotor (1) The finger notches used to turn the rotors to a start position (2) The alphabet RING or tyre round the circumference of the rotor (see below for an explanation of its significance) (3) The shaft upon which the rotors turn (4) The catch which locks the alphabet ring to the core (5) (5) The CORE containing the crosswiring between contactsEncryption with Caesar code is based on an alphabet shift (move of letters further in the alphabet), it is a monoalphabetic substitution cipher, ie a same letter is replaced with only one other (always the same for given cipher message) The most commonly used shift/offset is by 3 letters Enigma Machine ★ All Tools ★Enigma's Secrets How it Worked and How the Code was Broken By way of introduction, see the Historical Background to Enigma and the Key Players Involved The Working Principle The Enigma machine basically provided a simple substitution of a plaintext symbol with a different ciphertext symbol generated by the machine What made the machine special however was that



A More Complex Take On The Braille Alphabet To Encrypt Messages By Me Cryptography


The Human Errors That Defeated Enigma Openmind
Every alphabet has a number of symbols that are the building blocks of the specific language In addition to traditional written languages, alphabets have evolved for telegraphy (Morse code), visually impaired people (Braille) and maritime signal flagsMay 29, 19 · The enigma machine was used in World War II to encrypt secret messages The Enigma machines are a series of electromechanical rotor cipher machines The first machines were invented at the end of World War I by German engineer Arthur Scherbius and were mainly used to protect commercial, diplomatic and military communication Enigma machines becameMay 27, 21 · An Enigma machine is a famous encryption machine used by the Germans during WWII to transmit coded messages An Enigma machine allows for billions and billions of ways to encode a message, making it incredibly difficult for other nations to crack German codes during the war — for a time the code seemed unbreakable Alan Turing and other researchers exploited a



The Enigma 2



Pin By Lemon Zesst On zzz Ciphers And Codes Encrypted Messages Coding



Pin On Cryptography


Enigma The German Cipher Machine


Enigma And A Way To Its Decryption



Project 1 Enigma



In This Lesson We Will Understand Ppt Download


Exploring The Enigma Plus Maths Org



Codes And Ciphers Puts Students To Test Bryn Mawr Alumnae Bulletin



Enigma Daily Settings Generator 101 Computing



The Evolution Of Cryptography Part 2 The Dawn Of The Digital Age Luno


The Enigma Enigma How The Enigma Machine Worked Hackaday



Charlesreid1
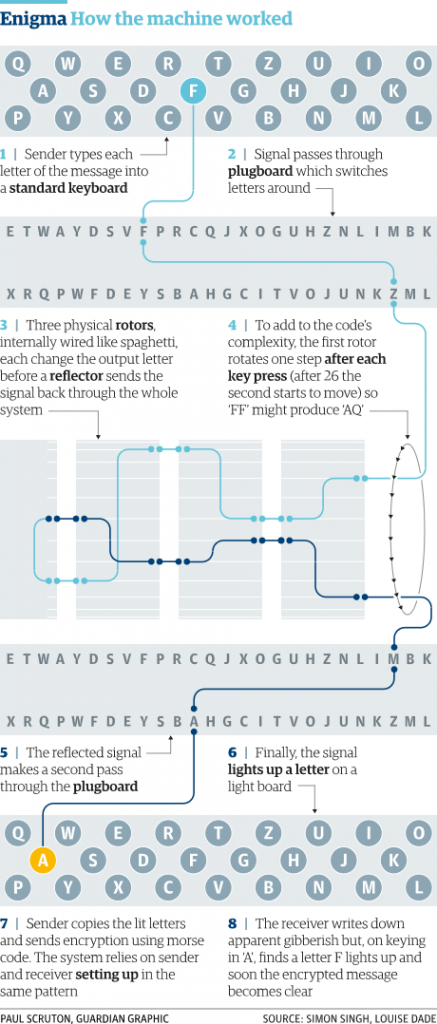


Sunday Science The Enigma Machine By Gemma Church Medium



Fer Al Enigma Language Codes


Description Of The Enigma


The World According To Benedict Cumberbatch Enigma Chapter 3 The Substitution Cipher


Red Luth Riddle Tools



Rotor Machine Wikiwand



How The Allies Cracked The Enigma Code By Karthick Nambi Lessons From History Medium



Cryptanalysis Of The Enigma Wikipedia



The Enigma 1



I Tried Using Paper Enigma Machine Which Can Reproduce Nazi Germany S Masterpiece Encryption Machine Enigma With Only One Sheet Of Paper Gigazine



Enigma Rotor Diagram Created By Wapcaplet In Blender Cc By Sa 3 0 Download Scientific Diagram
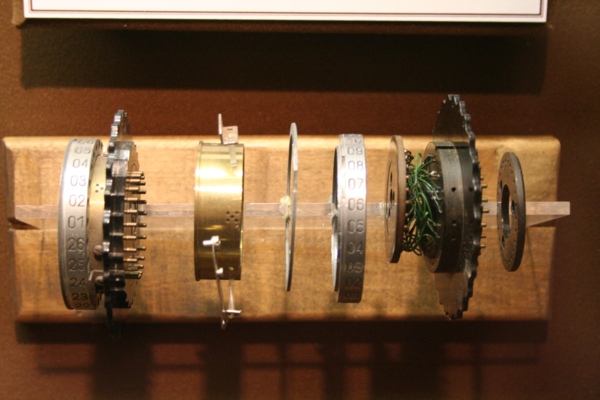


Enigma Rotor Details Wikipedia


The World According To Benedict Cumberbatch Enigma Chapter 3 The Substitution Cipher



Enigma Technology And The History Of Computers


The World According To Benedict Cumberbatch Enigma Chapter 3 The Substitution Cipher
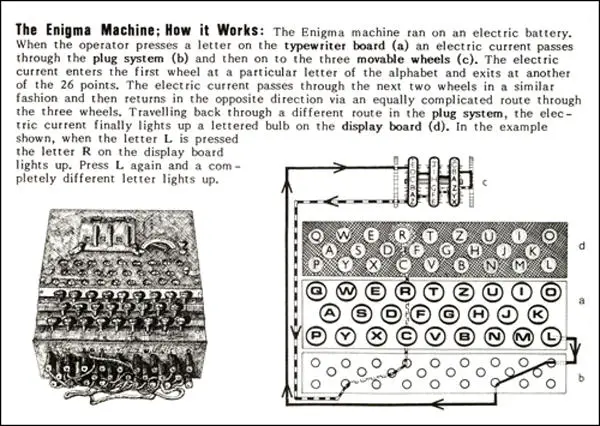


Enigma Machine



The Enigma 1
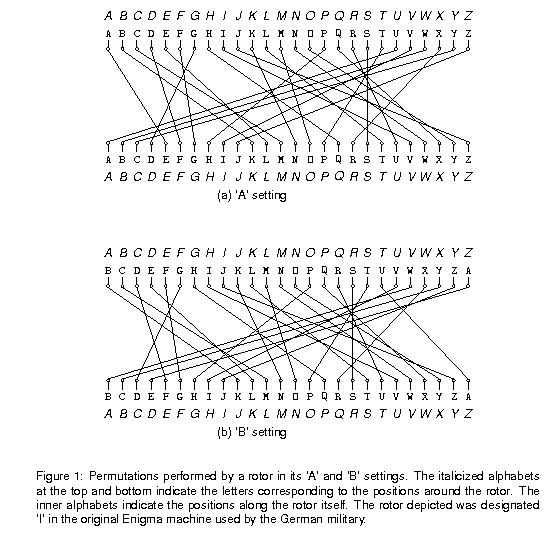


Project 1 Cs 61b Fall 16



The Enigma Cipher Machine And Breaking The Enigma Code
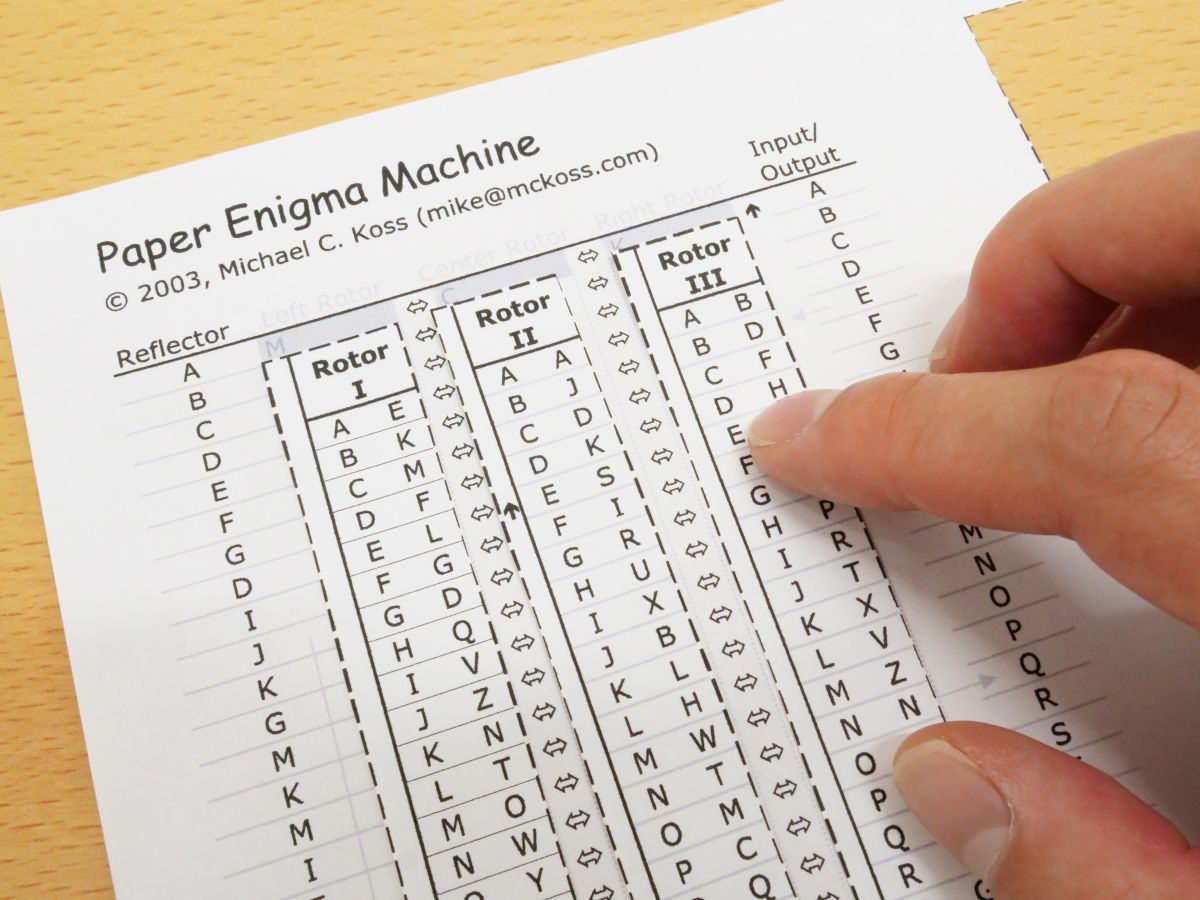


I Tried Using Paper Enigma Machine Which Can Reproduce Nazi Germany S Masterpiece Encryption Machine Enigma With Only One Sheet Of Paper Gigazine



10 Codes And Ciphers Commonly Used In History Ciphers And Codes Coding Coded Message


Enigma Cipher


Enigma Procedure


Red Luth Riddle Tools



Ic211 Oop And Enigma


The Enigma Machine And The Ultra Secret South African Military History Society


The Polish Attack On Enimga



Enigma 419 Painting By Numbers Enigmatic Code



Pin On Clues Games Escape Rooms
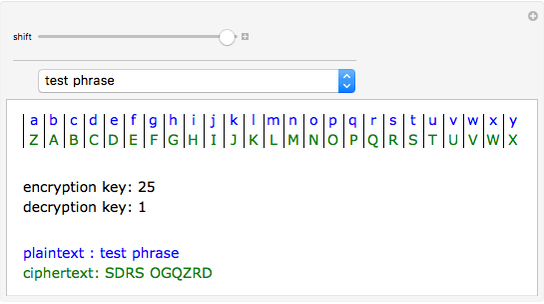


Additive Cipher Wolfram Demonstrations Project



Polyalphabetic Cipher Wikipedia



How The Allies Cracked The Enigma Code By Karthick Nambi Lessons From History Medium



The Enigma Cipher Machine And Breaking The Enigma Code
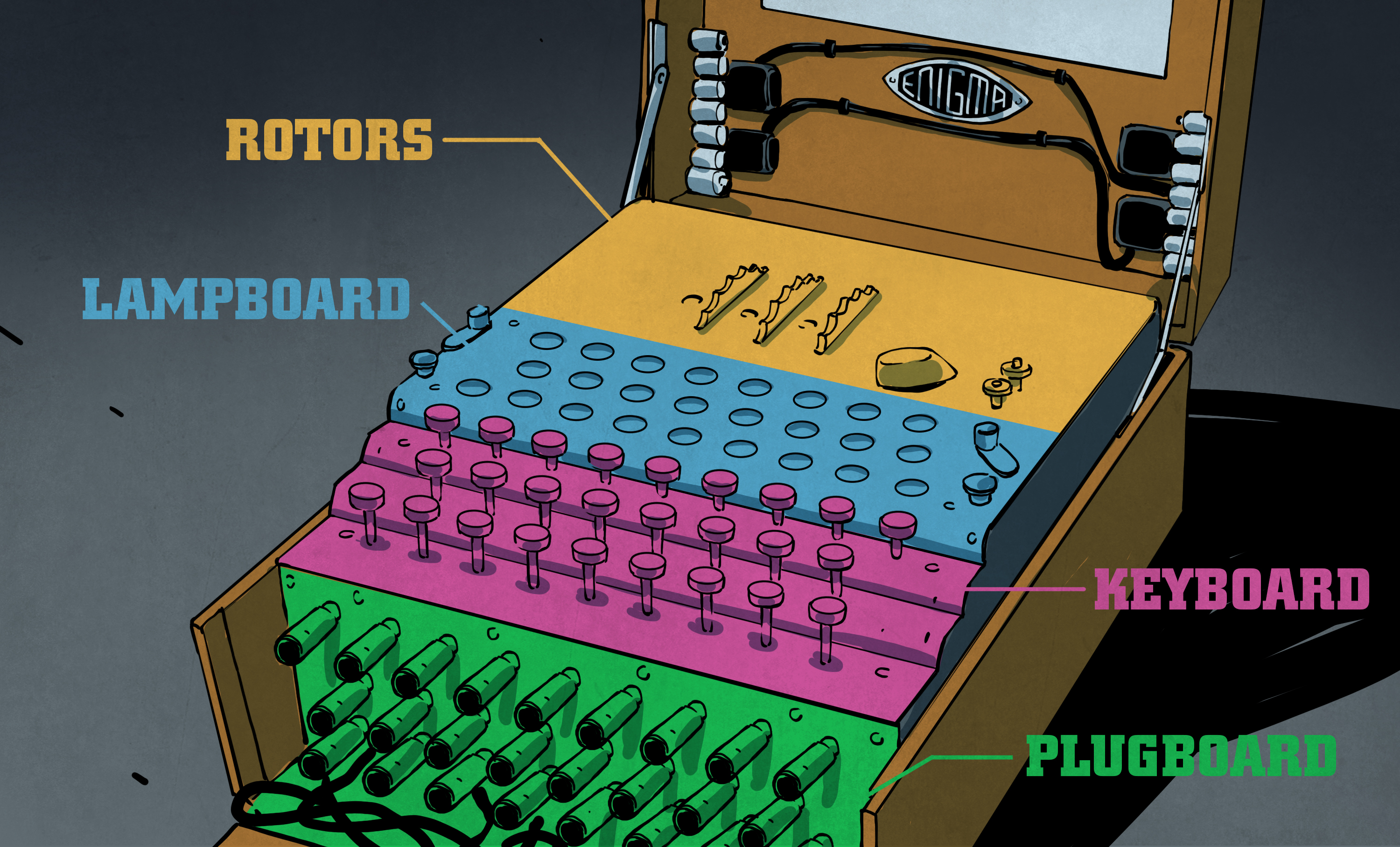


The Enigma Enigma How The Enigma Machine Worked Hackaday


Enigma


How Exactly Did The Enigma Machine Work How Did The Plugboard And The Rotors Change The Letters Quora
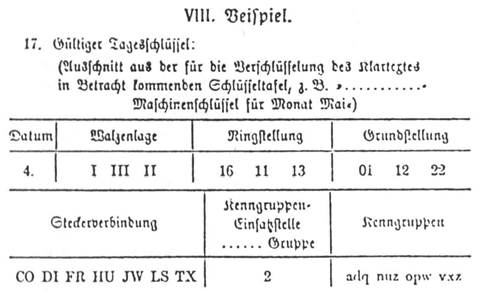


Enigma Codeproject
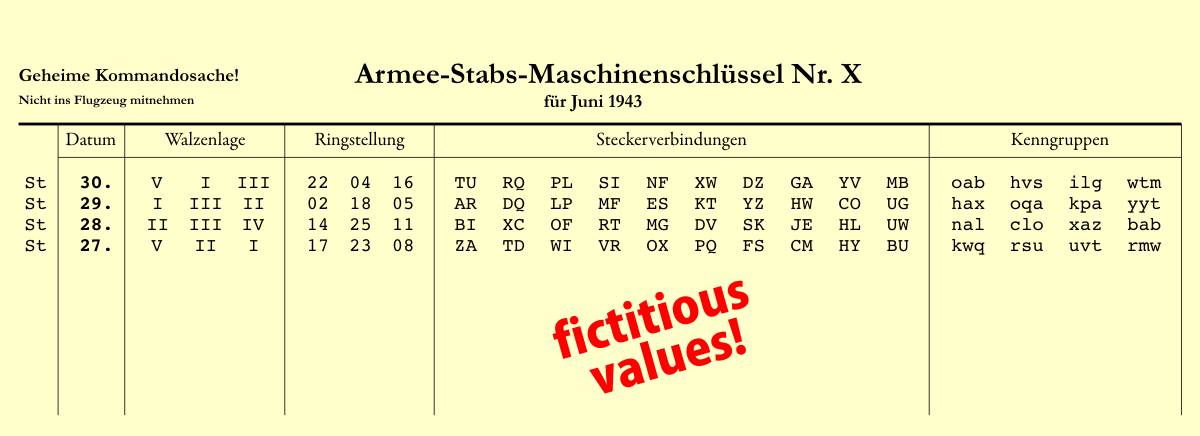


Enigma The German Cipher Machine


Enigma The German Cipher Machine


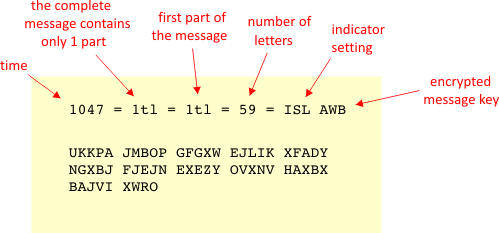
What Is The Enigma Code Quora
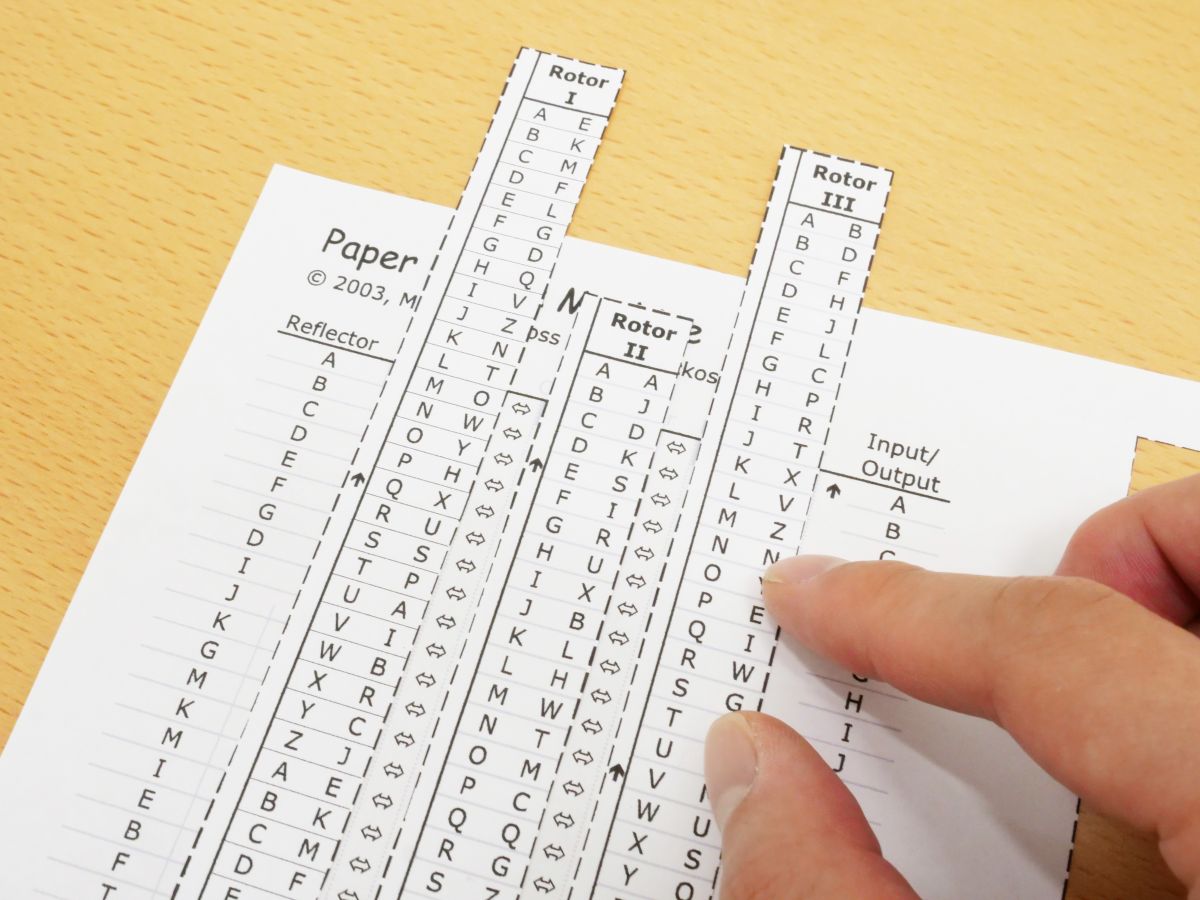


I Tried Using Paper Enigma Machine Which Can Reproduce Nazi Germany S Masterpiece Encryption Machine Enigma With Only One Sheet Of Paper Gigazine



Enigma Rotor Details Wikipedia



The Human Errors That Defeated Enigma Openmind



Enigma 2 World War Who Hacked The Enigma Code And When Who Could Decipher The Enigma Code



The National Archives Here S Something To Get Your Brain Working This Mondaymorning Encrypt And Crack A Code Using Alan Turing S Probability Based Method You Ll Need A Pencil Paper Scissors



Enigma
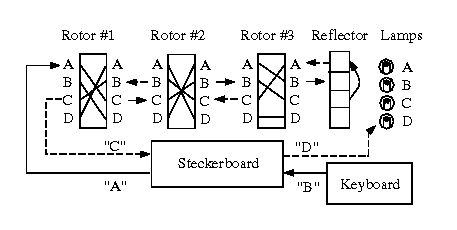


Cryptology I Vigenere Based Systems



Codes And Ciphers Puts Students To Test Bryn Mawr Alumnae Bulletin
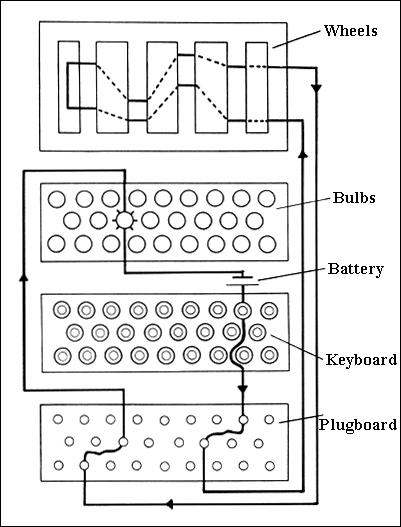


Enigma Machine



Enigma 1349 Alphabet Magic Enigmatic Code



The Human Errors That Defeated Enigma Openmind



Enigma Richard Gallon We Are Here



0 件のコメント:
コメントを投稿